What is a Brute Force Attack?
 I’ll provide a link to more info below but in case you don’t know, a brute force attack is not someone physically smashing your computer. A brute force attack is a software attack utilizing many servers to continually attempt to login to an account (in this case, a WordPress account) using common usernames and passwords like “user” and “password1234”. There’s no way to stop them from happening but you can discourage them and prevent them from being successful.
I’ll provide a link to more info below but in case you don’t know, a brute force attack is not someone physically smashing your computer. A brute force attack is a software attack utilizing many servers to continually attempt to login to an account (in this case, a WordPress account) using common usernames and passwords like “user” and “password1234”. There’s no way to stop them from happening but you can discourage them and prevent them from being successful.
How I Found Out
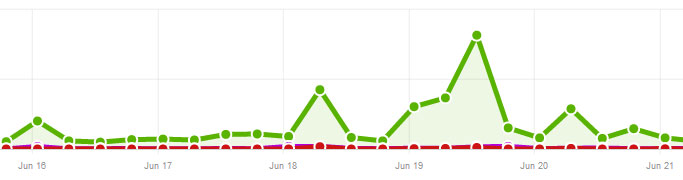
I check my traffic statistics with AW Stats every couple days at least. One day last week my traffic was 4x higher than a normal day. Since I didn’t see any more traffic from search engines or referral traffic from other websites so I had a feeling something was up.
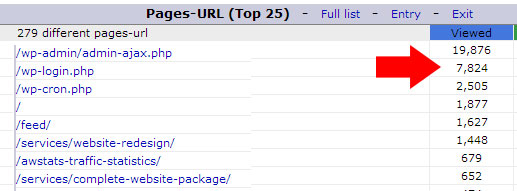
If you notice an unusual spike in traffic, the first place you can look is in your web statistics to see what pages are getting a lot of traffic. You can read my post on reading AW Stats and watch the video walk through to see how to view this information with most web hosts. In my case, I saw that wp-login.php, the page where you login to WordPress was getting a lot of views. I knew I wasn’t causing all those page views myself so there must be an attack against the site trying to login.
An Ounce of Prevention…
Luckily, I had read a few months prior about brute force login attempts against WordPress becoming very common and so I did some research and took action to secure my site in the event it happened to me. Here’s what I did and you should do the same if you have a WordPress site.
 1. Clean Up User Accounts
1. Clean Up User Accounts
Go through your user accounts in WordPress and delete any user accounts that are no longer being used. Also, make sure there are no users with obvious or default usernames like “admin” or “administrator”. As you’ll see below, those were the usernames the bots or programs were trying to use to login to my site.
2. Use Secure Passwords
Even if your username is unique, you must have a good password to ensure it cannot be easily guessed. You can use password generator like this to generate secure passwords. The longer and the more varied it is with numbers, symbols, and capitalization the more secure your site will be.
3. Install Security Plugin to Limit Login Attempts
There are a bunch of good security plugins for WordPress but after I did some research, I decided to install Wordfence because it has many security features in addition to the ability to limit login attempts by users with incorrect usernames and passwords. Wordfence ended up being a great help after the attack started as you’ll see below.
On Defense
 There’s no way to stop these attempts from happening but you can limit their success and impact by taking the steps above. Even though I wasn’t really worried about someone actually breaking into my WordPress site, I was annoyed by the number of hits to my website that were slowing down my hosting server for me and everyone else on my shared server. It’s also just not a good feeling being attacked.
There’s no way to stop these attempts from happening but you can limit their success and impact by taking the steps above. Even though I wasn’t really worried about someone actually breaking into my WordPress site, I was annoyed by the number of hits to my website that were slowing down my hosting server for me and everyone else on my shared server. It’s also just not a good feeling being attacked.
You’ve seen the movies set in medieval times where the enemy is storming the castle gate. The defending army isn’t usually inside the castle eating mutton chops and drinking a pint; they are usually a flurry of activity pouring hot oil or shooting flaming arrows at the enemy. Even though I wasn’t flinging anything high temperature, it was still enjoyable to have an active role in defending my site. Here’s what I did.
1. Contact Host and Monitor Bandwidth
One of the biggest dangers and annoyances when a brute force attack occurs against your site is the possibility of your site going down because your hosting provider limits the bandwidth. So you may want to check your bandwidth limit for the month to see how serious the attack is and if it’s possible your site could be shut down as a result. Then contact your host to let them know your site is being attacked and see if it is in danger of hitting any other usage limits.
In my case, I was at 10% bandwidth usage for the month and although the attack was hitting my site a lot, it was not using up a lot of bandwidth so I wasn’t worried about hitting that limit or my site going down. Having a plugin that limits login attempts like I mention above can help limit bandwidth usage by blocking out IP addresses that continually attempt to login unsuccessfully.
2. Watch The Action Live with WordFence
One cool feature of WordFence that I didn’t even realize was monitoring live traffic. You can turn on the live traffic monitoring in the settings and then go to the Live Traffic page and click on the Logins and Logouts tab to see the WordPress login attempts that are happening live. Here’s what the screen looked like for me:
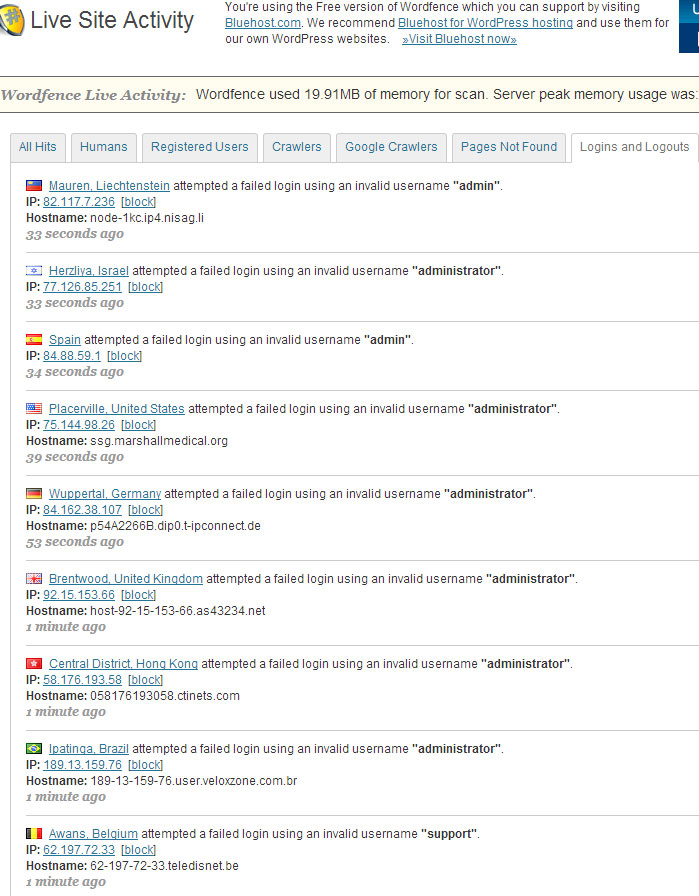
You can see the login attempts came from many different countries and IP addresses. Most of them use the username admin or administrator so you can see how important it is to NOT use those usernames for your WordPress login.
3. Block As Needed
 By watching the live login attempts and depending on how close you are to maxing out your monthly bandwidth, you can decide to take further steps. One of the best ways to keep these predators off your site in the first place is by blocking IP addresses. You can see in the screenshot above that you can do this in WordFence by clicking on the block links next to the IP addresses.
By watching the live login attempts and depending on how close you are to maxing out your monthly bandwidth, you can decide to take further steps. One of the best ways to keep these predators off your site in the first place is by blocking IP addresses. You can see in the screenshot above that you can do this in WordFence by clicking on the block links next to the IP addresses.
However, with each different login attempt coming from a unique IP addresses, this can be a tedious process and may not be worth the time. I decided to instead block entire countries that were the main culprits. You may or may not be able to do this in your hosting control panel but I use a proxy service called CloudFlare and their control panel allowed me to easily shut down entire countries from accessing my website. After I added 15 countries to the block list, it slowed down the login attempts very right away.
I obviously didn’t want to block the major countries that I get traffic from like US and Canada so for those countries I just blocked individual IP addresses or just left them since they weren’t producing many attempts anyway.
Blocking countries slowed down the login attempts on my blog from 1-2 per second to 1-2 every 10 minutes which I was comfortable with.
How Long Did It Last?
The brute force login attempts on my blog seemed to last for about 48 hrs. They slowed down drastically for a few days and then almost stopped completely. I have unblocked all the countries I had blocked and I do occasionally get login attempts on my WordPress site but they are so minimal that I don’t worry about them. If another large attack were to start, I would probably just block certain countries again.
UPDATE: Securing wp-login
A week after writing this post, I had another brute force login attempt start up on my blog. I decided to look into some of the steps I can take to block these login attempts completely. It seems that blocking access to wp-login using a second login layer is the best option.
This is a pretty technical process but I followed the directions from my hosting company Hostgator that they posted here and it seems to be working well. Basically, when I go to wp-admin on my domain, I get the following request to login with a second username and password I created.
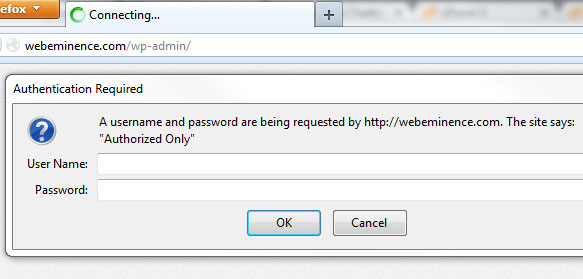
Since the brute force login scripts created by the hackers are setup to login to a WordPress login page, this second login should be enough to stop them in their tracks and keep them from ever reaching the WordPress login page and using up precious bandwidth. This is a little annoying for me because now I have to login twice but I can save both passwords in my browser and also turn this feature on ONLY when I’m experiencing a brute force login attack. You can probably follow the Hostgator support steps in my link above or talk to your hosting company about setting up something similar.
More Information and Recommendations
You can get more information on the WordPress.org page about Brute Froce Login Attempts. They have some other recommendations for securing your WordPress site that I didn’t mention here like password protecting wp-login or only allowing access to your IP address. These would be great options if you are having repeated attempts that are not slowing down.
What was your experience with a brute force login attempt on you WordPress site or blog? I know that every attack is a little different so share your experience in the comment section below or let me know if you have any questions about mine.
